Celluster™ AI Fabric Immune System
Protecting GPUs, NVLink & RoCE from DoS / NoS.Most “AI security” tools stop at pods, VMs, APIs, or models. Meanwhile, attackers can quietly drain GPUs, saturate NVLink, or flood RoCE, turning an AI cluster into a very expensive heater while dashboards stay green.
Celluster is an AI fabric immune system: Reflex Cells sit beside GPUs and NICs, enforcing declared intent and shutting down DoS / NoS at the hardware edge, before it becomes an outage.
The Category
Celluster = Fabric Immune System, not another scanner.
Celluster is not runtime scanning, not EDR, and not a container or model security product. It is a reflexive substrate that makes NVLink, RoCE and GPU fabrics self-defending.
Think of it as: “immune system for the AI fabric”
sitting under today’s clusters and meshes, enforcing intent where packets and DMA actually flow.
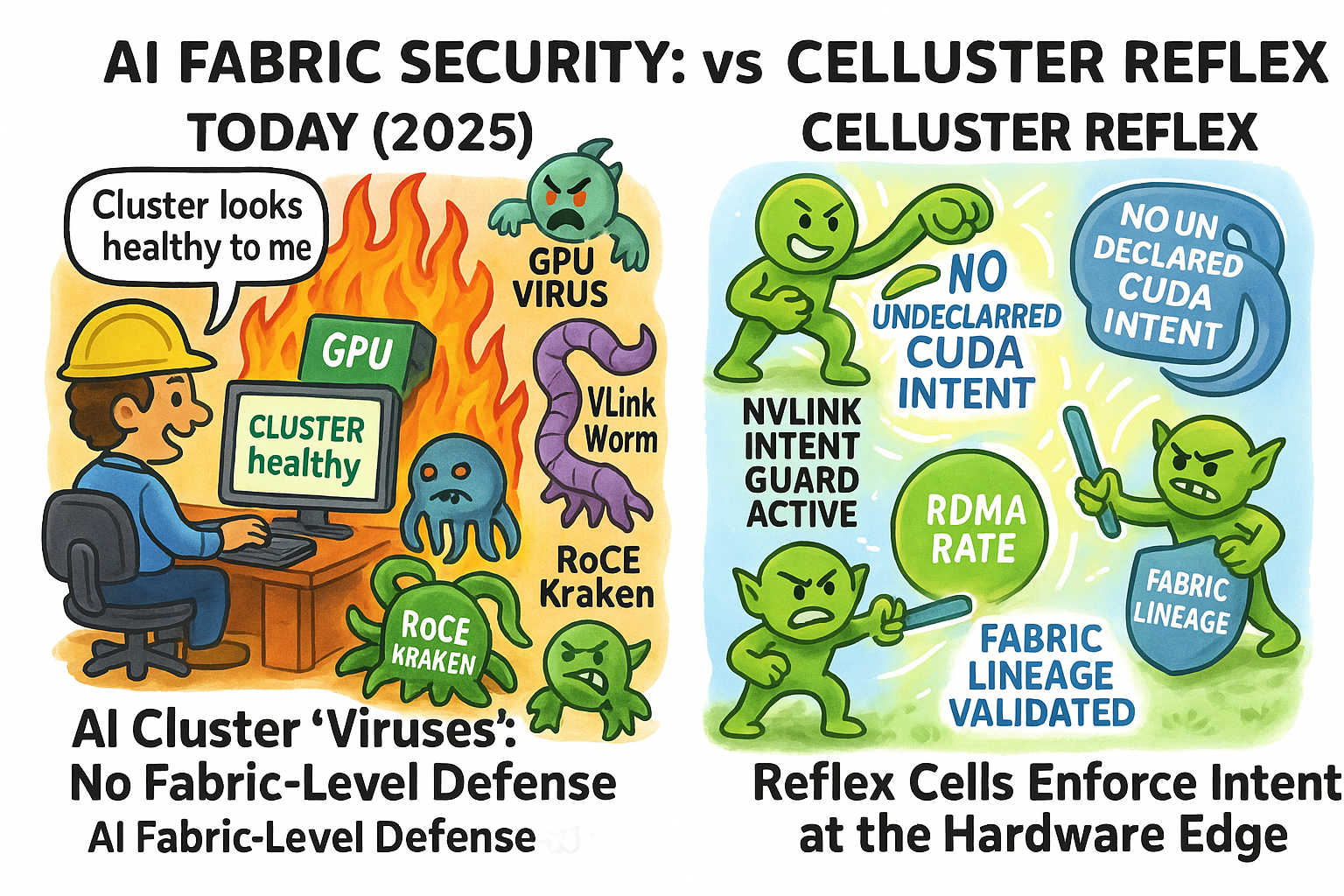
Right: Reflex Cells enforcing intent at the GPU, NVLink and RoCE edge — a true fabric immune system.
AI Cluster & Fabric DoS / NoS
When the GPUs are melting, the logs still look fine.
A modern attacker doesn’t need a science-fiction “AI virus.” They just need to turn your AI fabric against you:
- GPU DoS: wasteful kernels keep SMs at 100% and VRAM exhausted.
- Thermal pressure: sustained overload forces throttling and node dropouts.
- NVLink saturation: pointless traffic keeps gradient sync permanently late.
- RoCE / RDMA floods: low-value memory transfers clog east–west bandwidth.
To users and SREs, this just looks like “the cluster is slow today.” To an attacker, it’s a very quiet, very effective DoS.
Pods are fine. TLS is fine. Dashboards are green. The fabric is on fire.
Why Today’s Stack Can’t See It
Workload security ≠ fabric security.
Most tooling was built for CPU-era problems and control planes:
- Kubernetes / Slurm: schedule jobs; they don’t understand NVLink or RDMA intent.
- SDN / meshes: enforce L3/L4/L7 policy; the fabric is just “fast pipes.”
- EDR / workload agents: see processes and syscalls, not GPU training flows.
- Control planes: react at API and human speeds, not at fabric speeds.
We have excellent research on side-channels, timing and vulnerabilities — but production defenses are still glued to pods, IPs and YAML.
In other words: we built a helmet for the rider and forgot the brakes on the bike.
Celluster: Reflex Cells on the Fabric
From “observe and pray” → to “detect and reflex.”
Celluster introduces Reflex Cells as a substrate that lives beside GPUs, NICs and fabrics — not just in front of services.
Each Cell carries:
- Identity: who this Cell is.
- Intent: how much GPU / fabric it should consume and how.
- Lineage: where it came from — which tenant, app family, or job.
- Reflex rules: what to do when behavior doesn’t match intent.
Instead of waiting for a controller to notice a problem, the fabric reacts locally:
- Misbehaving Cells can be isolated or decayed at the edge.
- Suspicious patterns trigger rate limits or reroutes in milliseconds.
- Healthy Cells continue uninterrupted; only the noisy lineage gets contained.
Today’s Defenses vs Fabric-Native Reflex
What changes when security becomes part of the substrate.
| Attack Type | Today’s Reality | With Celluster Reflex Cells |
|---|---|---|
| GPU compute flood | Cluster slows down; looks like “busy but healthy.” | Usage that violates intent is pinned to a lineage and automatically constrained or shut down. |
| NVLink saturation | Training jobs miss windows; root cause unclear. | Cells causing abnormal intra-node chatter are slowed or isolated before they starve everyone else. |
| RoCE / RDMA flood | Inter-node congestion, timeouts, paging SREs at 3am. | Reflex rules cut low-value fabric traffic from the offending Cells before congestion cascades. |
| Cryptojacking on GPUs | Looks like “high utilization” in dashboards. | Patterns that don’t match declared intent are flagged and decayed automatically. |
Outages as Comic Relief (Until They’re Real)
What the comic shows — and why it matters.

Right: Reflex Cells quietly enforcing intent on the fabric in real-time.
The cartoon is funny because it’s true: most AI outages start in places our tools don’t look. Celluster’s claim is simple:
Don’t bolt “AI security” onto the side.
Make the AI fabric itself reflexive and self-protecting.